I learned my first SAML integration in 2005 using a product called SHARE-id developed by Oblix that was later part of IAM product suite of Oracle. Last 10 years there is a huge adaption of SAML protocol for a seamless integration with a centralized Authentication service providers like Azure, Ping, Forgerock, Google and so on. You can also write your own Authentication service supporting SAML. Its is easy to find free library to implement a SAML IDP (Identity Provider) or SAML Assertion consumption service for a SP (Service Provider).
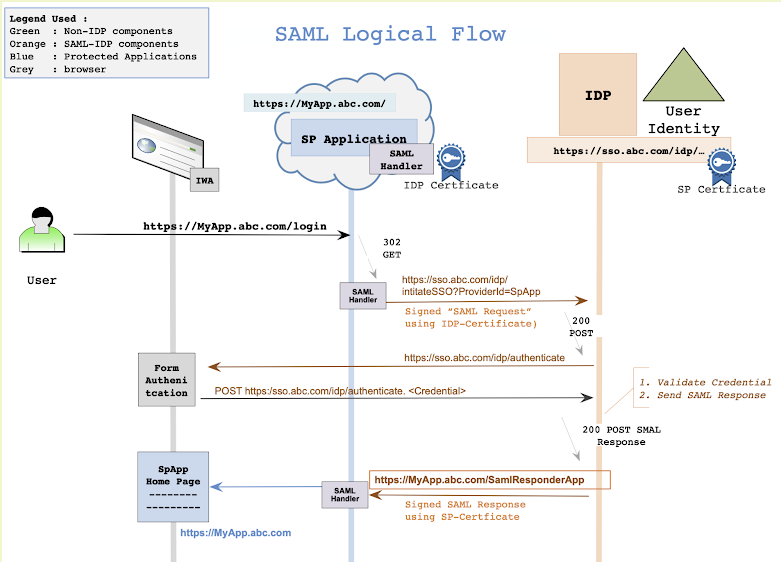
Here is a diagram of a standard SAML flow.
I will not describe how SAML integration work as many good articles are already available in the net. This write-up specifically focus on "Certificate Renewal" aspect of SAML integration. It is one of the major pain point in SAML integration.
Context :-
One or many Service-Providers (SP/ web application) tied to a Identity-Provider (IDP/ Azure, Forgerock, ping, home-grown) in a “Circle of Trust”, where IDP shares the certificate with all SPs. SP uses this certificate to verify the digital signature in SAML-Response that proves that it has indeed come from the chosen IDP.
Now the Issue :-
Just like any other certificate, IDP’s certificate also expires every 3yrs. All the participating SP need to replace the expired cert with the new one. When you have 100+ SAML apps in production, co-ordinating with so many AppOwners and getting the cert replaced requires good amount of planning and effort
Possible Solutions :-
(1) Plan it out in advance :-
This is the bare minimum an IDP owner can do :-
o Add a new certificate to each IDP in non-prod env 3 months before the expiry. Coexistence of “to-be-expired” certificate with “new” certificate ensure no outage.
o The new cert (and/or IDP-metadata) then distributed to each AppOwner.
o The expired certificate is removed from the IDP once all AppOwners confirm that their app's SAML integration is working with new certificate.
o Same processes followed in production.
(2) Can we improve this process and automate it ?
Yes, all depends on your organization budget though :) An IDP-Application-dashboard portal can be built where App-Owners can seamlessly onboard their SAML compatible application thru user friendly App registration process.
o IDP owner proactively add the new certificate to the IDP before the expiry and portal then notify the app-owners.
o App-owners picks up the certificate and DP meta data and test the SAML integration.
o The portal then remove the old certificate from IDP immediately after app-owner certify the successful integration using the new certificate.
Basically, the portal replace the the manual co-ordination between IDP-Owner and App-Owner by automating the IDP cert renewal process.
(3) Any other Options?
Yes, switch to OIDC based integration, which is based on light weight token compared to XML heavy SAML response. OIDC token is signed using either a client-secret or jwks (Json Web Key). We will cover this in the next blog.